Here we will describe an example of key management based on a smart card system. The purpose is to further illustrate the principles described above with a more easily understood set of examples. Compared to this example, real large systems are often more complex and have several levels of structure. Smaller systems usually do not require any key hierarchy because a secret global key is used for all cards. The system presented here is in the middle of a large system and a system with a simple structure, so it is a good example. The top-level key is called the universal master key, and there is only one such key for the entire generation of keys. For example, the generation can remain valid for one year and can be replaced with a new generation in successive years. This is the new generation of universal master keys. This key is the most security-critical key in the entire system. If it is known, all the keys belonging to its generation can be calculated, and the generation of the system is broken. The master key may be generated by a random number, and it is also conceivable that the universal master key is formed by the value obtained by each of the individuals individually rolling the dice, wherein each person only knows the partial value of the key, and the universal master key should never be Any individual individual is fully aware, and in its generation there must be no conditions that can be reproduced. Looking at the system in this example seems a bit complicated, but it is still relatively simple compared to the actual system. The purpose of this example is to show how all the keys in a system are generated. It also implies a method that must be taken if a key is known. If the universal master key is known, it must be switched to a new generation so that the system can operate without having to consider the security risks. On the other hand, if a derived key is known, what is needed is to lock the relevant card, and any other changes to the key management are not appropriate. All of these methods assume the premise of being able to determine that one (or several) keys are known and can be prevented in the future.
Product
Features
Used
commonly in construction and utility, mason Twine features a smooth
construction that ties easily and knots securely. High-visibility twine offers
good resistance to abrasion, UV light, rot, mildew. The braid twine is commonly
used in building, so it is also called build line,building line,mason twine.
• High strength, high visibility
• For construction, utility and more
ITEM NO.
DIAMETER
LENGTH
N.W
UNITS
200320
# 15
375'
1/4 lb
12
200321
# 15
570'
1/2 lb
12
200322
# 18
275'
1/4 lb
12
200323
# 18
550'
1/2 lb
12
200324
# 18
1100'
1 lb
12
200325
# 36
120'
1/4 lb
12
200326
# 36
480'
1 lb
12
Product
Application
Most
products used in agriculture, building, as to the building line, fishing line.
FAQ:
Q: How about payment terms?
A: 30% TT deposit + 70% TT against the B/L copy
within 3 days.
Q.:What about the lead time?
A: We need 3-7 days to get the samples
ready, for bulk goods, it will cost 15-60days,up to the quantity.
Braided Twine,Customized Braided Twine,Colorful Braided Twine,Braided Nylon Twine ROPENET GROUP CO.,LTD , https://www.cnparacord.com
In the example of Figure 1, the keys for loading or paying can be used for electronic wallets, which use symmetric encryption methods, which are important in any case in the system because they are better The key hierarchy is protected. The various export functions are not detailed here, but DES or 3 DES algorithms are always available for them. The length of the keys is not discussed in detail, but they are indeed variable. For security reasons, keys at the top level of the hierarchy are usually exported with more powerful encryption than their lower-level keys. .jpg)
Figure 1 Example of key hierarchy for smart card systems and symmetric encryption algorithms
The separate master key for each function is derived from the universal master key, which can be a function of loading or paying for an electronic wallet. A one-way function, such as a variant DES algorithm, can be used in this example to derive the master key for each function, which makes it impossible to apply the reverse computation process to the master master key from the master key. If you do not use a one-way function to export the master key, although there are various security methods, if a master key becomes known, if you know the export parameters, you can calculate the universal master key. The reason for using a one-way function here is to assume that in this imaginary e-wallet system, the master key will be located in the security module of the local terminal. That is to say, they are more vulnerable to attack than the universal master key that is always in the background system.
The derived key forms the next layer in the key hierarchy, which is the key located in the smart card. Each card contains a set of derived keys that are separated by their function and toward the "generation" number. If such a card is used for the terminal, the parameter terminal used to derive the key can calculate the derived key for itself. Of course, the terminal first needs to read the derived parameters from the card. Once the derived key is available, the following steps are taken to calculate the dynamic key, which is specific to a single session. This key is only valid during a single session. In most smart card applications, the duration of the session can range from a few hundred milliseconds to a few seconds, and this dynamic key is no longer used after the session ends.
The key layer of this e-wallet system is shown in Figure 2. 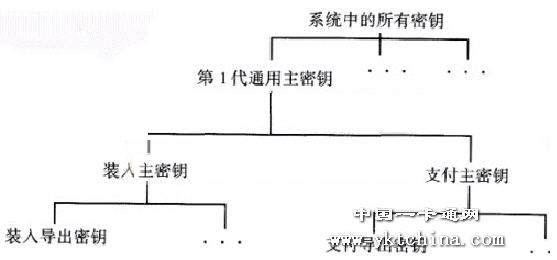
00000000Fig. 2 Example of key for e-wallet system
Given this level of keying, it is clear that many keys are generated and stored in the smart card. Of course, in order to save storage space, it is always possible to specify several functions to share a single key, and it is also possible to envisage different key hierarchy arrangements. This of course depends to a large extent on the key management of the system.



Key management example based on smart card system